When David Cullen took up the job of Principal Advisor of Cyber Incidents and Emergency Management at the Victorian Department of Premier and Cabinet a year ago he was told there had been just 13 cyber-attacks in the history of the organisation.
“I scratched my head and thought, ‘what a ripping job I’ve landed in’,” he told delegates at a Technology in Government conference in Canberra last week.
He soon found out those 13 attacks weren’t “even close to the tip of the iceberg”.
After conducting a whole of government survey it became apparent that hackers were attempting to breach government systems every 45 seconds and that nine in 10 Victorian government organisations had experienced a cyber incident.
From organised crime to political hacktivist and online vandals, government systems were under attack from thousands of online threats including phishing attacks, malware and more.
Some of these saw Victorian departments make headlines – from theft of employee information to an emergency service data breaches.
As well as causing reputational damage, the attacks were having massive impacts on agencies – with three in four government organisations experiencing disruption to their systems or services and one in 10 losing personal information.
“What we suffered from was an inability to firstly understand our threat environment and appreciate how significant it was, and capture data about it that allowed us to make proper decisions about how we best respond to it,” he said.
Cyber-paramedics take the charge
Knowing that the government’s approach to cyber threats had to radically change, the government introduced a cyber incident response service.
“Its sole purpose is to provide government organisations a helping and hand when something goes wrong – we’re Victoria’s cyber-paramedics – we’re there 24/7 to support government organisations that experience an incident,” Mr Cullen said.
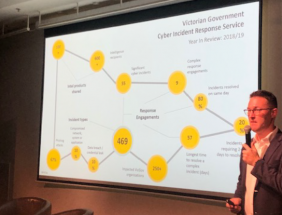
In the past 12 months the service has responded to nearly 470 cyber incidents, affecting more than 250 Victorian government organisations.
“How did we respond? Sometimes it was simply giving advice over the phone. In other cases it took a more complex response effort,” he said.
The cyber-response team also compiled more than 100 cyber intelligence products to help agencies mitigate harm and prevent incidents occuring.
Now, the team is set to boost their cyber response even more, positioning Australian cyber emergency response specialists AusCert to be the government’s main cyber security help desk.
Lessons from the ‘cyber-paramedics’
From investing in your human assets to being transparent if something goes wrong, Mr Cullen says there’s a lot to be learnt from the past year in Victorian cybersecurity.
One crucial lesson, he says, is not underestimating the power of phishing attacks – fraudulent attempts to harvest sensitive information by agents purporting to be a legitimate organisation.
“One interesting conversation we’re having across the Victorian Government now is about not downplaying the significance or risk of phishing. It’s often trivialised,” he told the conference.
“The truth is it’s a big deal because it’s the gateway for so many other attack types including ransomware, data breaches and email compromise and denial of service.”
Being candid if something does go wrong is also essential, according to Mr Cullen.
“What I think is most important is transparency, openness and honesty when a breach occurs. Come out and tell people you’re sorry. Don’t hide it or sweep it under the rug, be honest and quick and upfront about what they need to do to keep themselves safe online.
“Don’t be a hero. You can’t do it all on your own and if you think you can it won’t work and the harm you are there to prevent will eventuate. Find someone you trust and someone you can partner with and don’t be afraid to ask for help when things go wrong.”




My experience of 10+ years in the Victorian Govt sector was security theatre at it’s best. Let’s been seen to be doing the right thing, rather than actually doing it. That way they get to save money can be saved for more important things like paying managers to do expensive overseas business courses, or spending 70+ to renovate a floor in the building because the Dept Secretary wants to leave his stamp on the Department. Don’t be mislead in to thinking strides in Cyber Security are being made.